Cybersecurity – Protecting Your Business in the Digital Age
by admin

In this digital era, cybersecurity has become an important element of IT’s strategy. Currently, businesses face an increasing number of cyber threats that can compromise sensitive information, and cause significant financial losses.
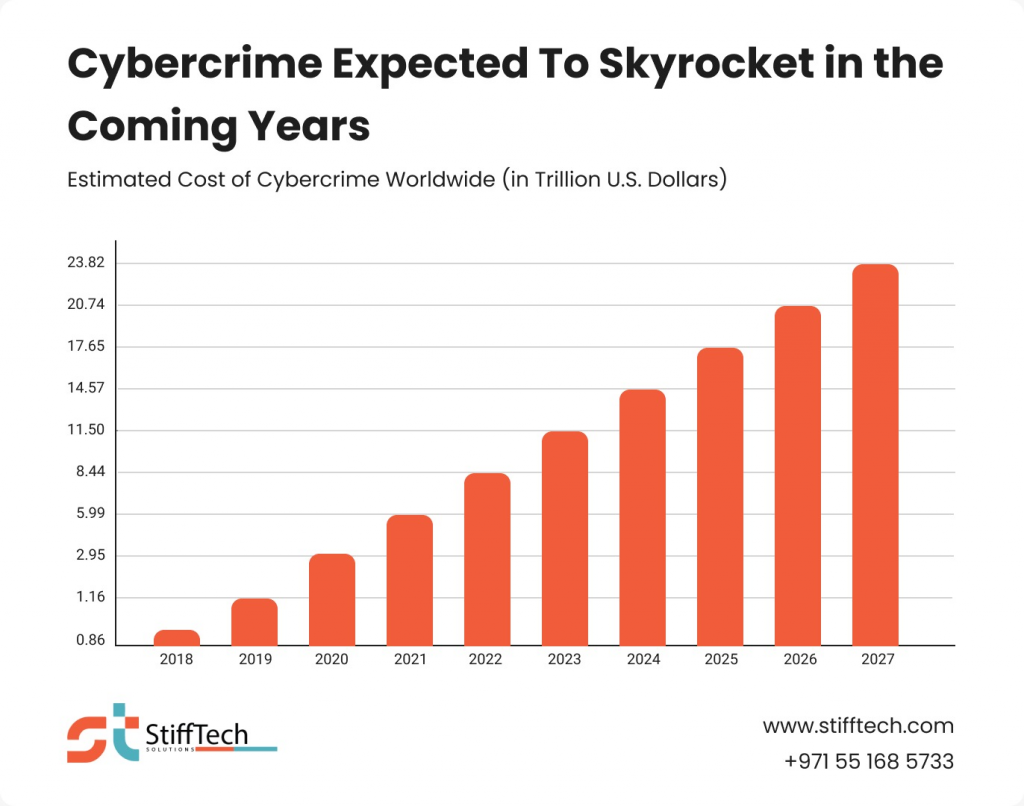
As per projections in Statista’s Cybersecurity Outlook, cybercrime will witness a substantial increase in the upcoming five years, escalating from $8.44 trillion in 2022 to a staggering $23.84 trillion by the year 2027.
“Cyber criminals can use personal details, such as your favorite color, the last four digits of your credit card and your email addresses, to make educated guesses about your sign-in credentials.”
—Larry Alton
Elements of Cybersecurity
Cybersecurity encompasses various elements and practices aimed at protecting digital systems. Here are some key elements of cybersecurity that can help you for your organization:
Data Security
Data security focuses on protecting sensitive and valuable data from unauthorized access. It includes measures such as data encryption, access controls, data loss prevention (DLP) solutions, and secure data backup and recovery processes.
Network Security
Network security refers to the measures and practices implemented to protect computer networks from malicious traffic. It is important to regularly assess and update network security measures to stay ahead of evolving threats and maintain a strong security posture.
Here are some key aspects of network security:
- Firewalls
- Virtual Private Networks (VPN)
- Network Segmentation
- Access Control
- Wireless Network Security
Endpoint Security
Endpoint security involves securing individual devices, such as computers, laptops, smartphones, and tablets, that connect to a network. They are often the target of attacks, making it crucial to secure them to prevent data breaches, unauthorized access, and other malicious activities.
Application Security
Application security aims to identify and address vulnerabilities in software applications. It refers to the practices and measures taken to ensure the security and integrity of software applications.
Identity and Access Management (IAM)
Identity and Access Management (IAM) refers to the processes, technologies, and policies used to manage and control access to digital resources within an organization. By centralizing identity and access control, organizations can reduce the risk of unauthorized access.
Incident Response
Incident response is an organized approach to managing and addressing cybersecurity incidents.The goal of incident response is to minimize damage, and restore normal operations. Another main goal is to learn from the incident to prevent future occurrences.
Security Awareness and Training
Security awareness training is a strategy used by security professionals and IT employees to reduce the risk of breaches. They aim to educate employees and users about potential security threats, and the importance of following security procedures.

Threat Intelligence
It involves collecting, analyzing, and interpreting data from various sources. This helps them to identify and understand cybersecurity threats and take appropriate measures to threat prevention.
Vulnerability Management
Vulnerability management is a crucial component of effective cybersecurity. It helps minimize the likelihood of successful attacks, protect sensitive data, and maintain the integrity of critical systems.
It involves the following steps:
- Vulnerability Discovery
- Vulnerability Assessment
- Risk Prioritization
- Remediation Planning
- Patch Management
- Mitigation and Controls
- Continuous Monitoring and Retesting
Security Governance and Compliance
Security governance and compliance are essential aspects of effective cybersecurity management within organizations.
Security Governance
Security governance sets the direction, goals, and objectives for the organization’s security program. It refers to the framework and security measures that enable organizations to manage their cybersecurity efforts effectively.
Compliance
Compliance refers to adhering to relevant laws, regulations, and industry standards related to information security. Organizations must develop policies, procedures, and controls to meet these requirements and ensure ongoing compliance.

What is Phishing in Cybersecurity
Phishing is a form of cyberattack where attackers send information or assets to the wrong people. Phishing attacks typically occur through various communication channels, including email, instant messaging, social media, or phone calls. Successful attacks can lead to data breaches.
Link Phishing
Link phishing refers to a technique used by cybercriminals to deceive individuals into clicking on malicious links that lead to downloading malware. It’s essential to educate employees and individuals about the dangers of phishing and how to avoid suspicious links.
Phishing https
Phishing HTTPS involves attackers using secure website (HTTPS) connections to trick individuals into downloading malicious content. It highlights the importance of not solely relying on the presence of HTTPS in determining the legitimacy of a website.
Crime Phishing
Crime phishing typically refers to phishing attacks aimed at obtaining personal or financial information for fraudulent purposes. It emphasizes the criminal intent behind phishing activities.
Malware Phishing
Malware phishing uses phishing techniques to deliver malware, such as viruses to compromise systems or steal data. It’s crucial to implement strong malware detection and prevention mechanisms to defend against such attacks.
Business protection in Cybersecurity
Business protection involves a comprehensive approach to minimize risks, prevent unauthorized access, detect and respond to security incidents.
Key Elements of Business Protection
Here are some key elements of business protection in cybersecurity:
Risk Assessment
Conduct a thorough assessment to identify and understand the specific cybersecurity risks faced by the business. This includes assessing vulnerabilities, threats, and potential impacts on systems, data, and operations.
Security Policies and Procedures
Establish security policies and procedures that outline the organization’s guidelines, and requirements for information security. These policies cover areas such as data classification, access controls, password management, and acceptable use of technology resources
Network Security
Regularly monitor network traffic, apply security updates, and segment networks to limit the potential impact of security breaches.
Data Protection
Implement encryption, data backup, and recovery measures to safeguard sensitive data. Establish data backup and recovery processes to ensure data availability and integrity during system failure.
Compliance Regulations and Standards
Stay up-to-date with relevant cybersecurity regulations, industry standards, and best practices applicable to your industry. Comply with legal and regulatory requirements related to data protection and privacy.
Information Protection in Cybersecurity
Information protection is a critical aspect of cybersecurity that focuses on safeguarding sensitive and valuable information. Organizations can mitigate the risk of data breaches, and instill trust among customers and stakeholders.
Conclusion
By investing in cybersecurity, individuals and organizations can get a secured environment. It ensures the protection of your sensitive information, maintaining business continuity, fostering trust, and contributing to a safer and more secure digital ecosystem.
“If you think technology can solve your security problems, then you don’t understand the problems and you don’t understand the technology.”
—Bruce Schneier
For more information visit www.stifftech.com
Recommended Posts

14 Best WordPress Development Agencies (2023)
May 2, 2024

E-Commerce website design company in Dubai
November 30, 2023

5 Types of Website Designs: Key Features & Functions
November 23, 2023
